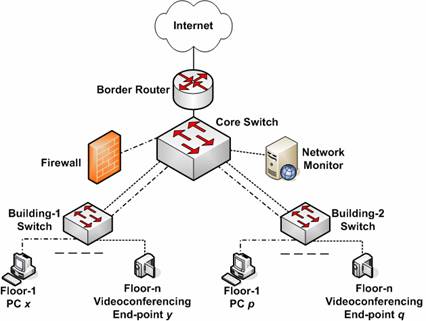
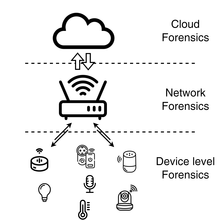
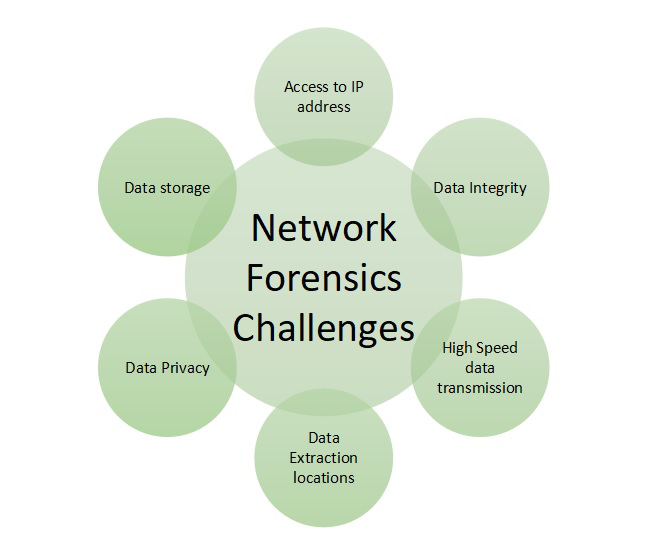
GitHub - mesquidar/ForensicsTools: A list of free and open forensics analysis tools and other resources

Buy Hands-On Network Forensics: Investigate network attacks and find evidence using common network forensic tools Book Online at Low Prices in India | Hands-On Network Forensics: Investigate network attacks and find evidence