Backdoor Shop Los Perros Volantes Freestyle Jam - Photo de Backdoor Snowboard | Ski | Bike | Running Shop, Grindelwald - Tripadvisor
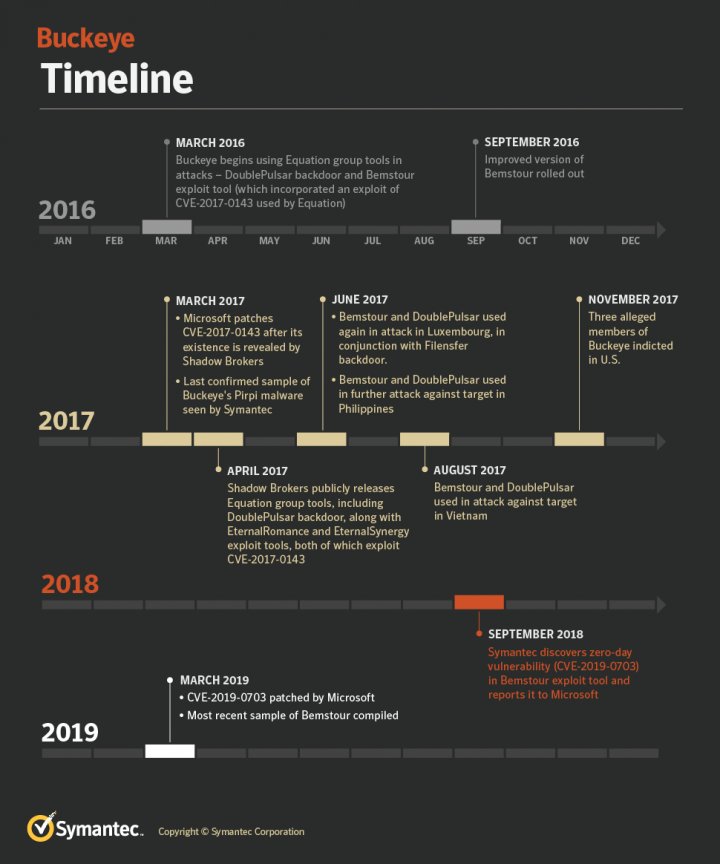
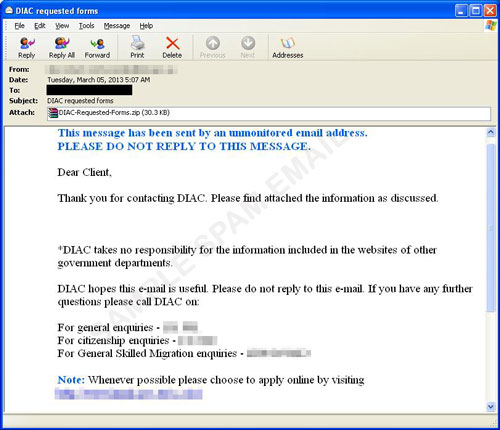
Buckeye: Espionage Outfit Used Equation Group Tools Prior to Shadow Brokers Leak | Symantec Enterprise Blogs
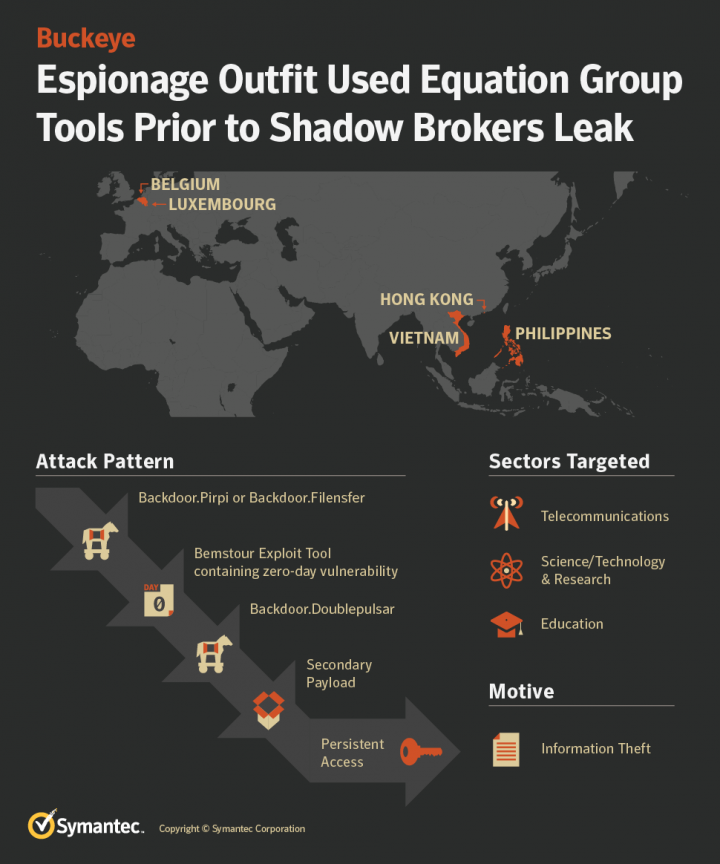
Buckeye: Espionage Outfit Used Equation Group Tools Prior to Shadow Brokers Leak | Symantec Enterprise Blogs

Villain - Windows And Linux Backdoor Generator And Multi-Session Handler That Allows Users To Connect With Sibling Servers And Share Their Backdoor Sessions
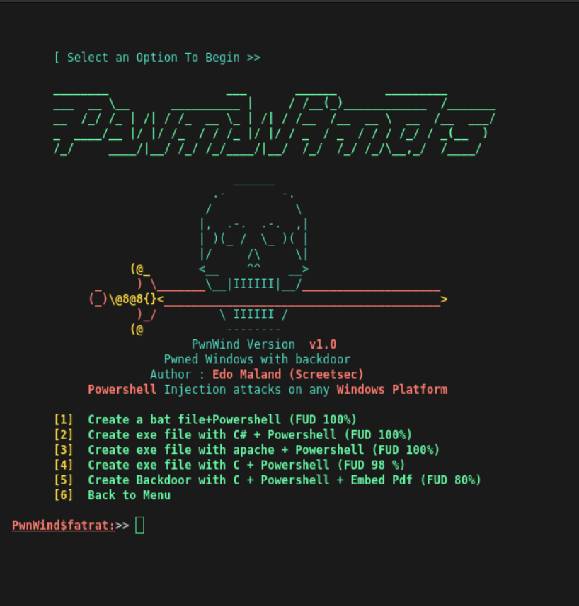
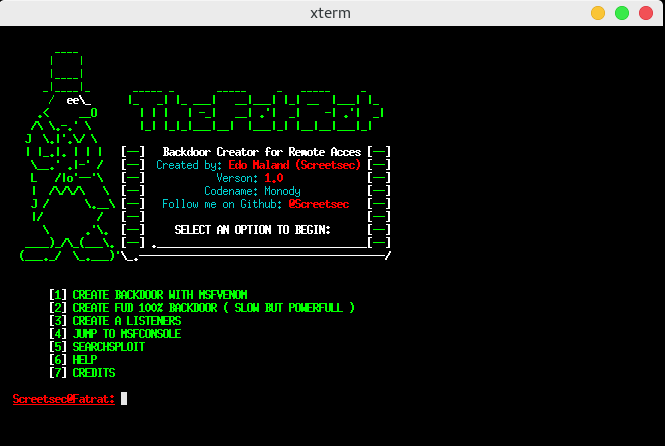
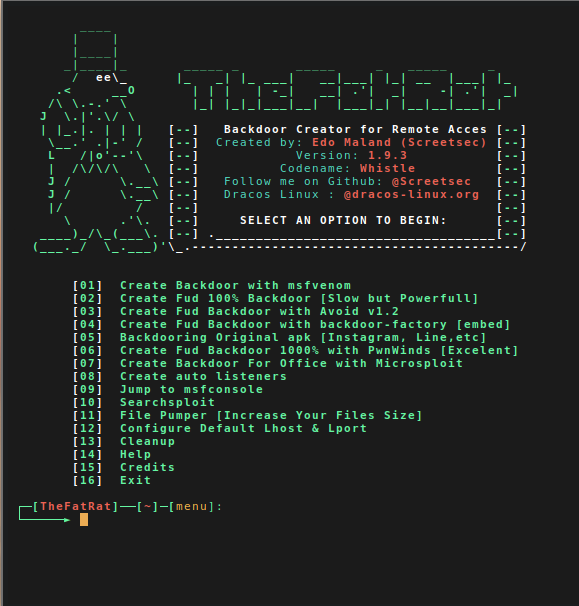
GitHub - screetsec/TheFatRat: Thefatrat a massive exploiting tool : Easy tool to generate backdoor and easy tool to post exploitation attack like browser attack and etc . This tool compiles a malware


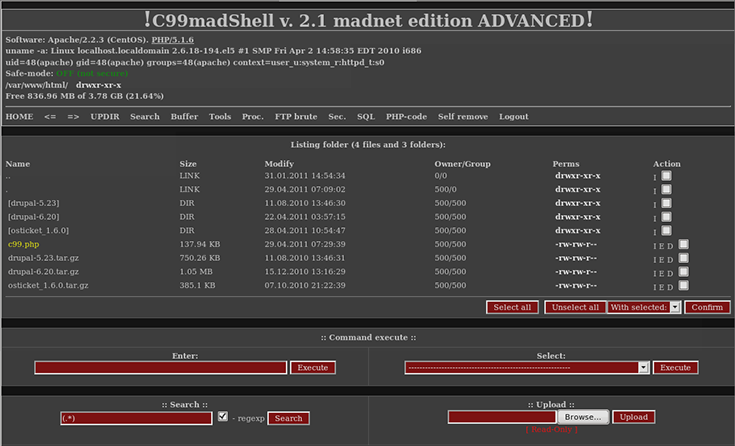
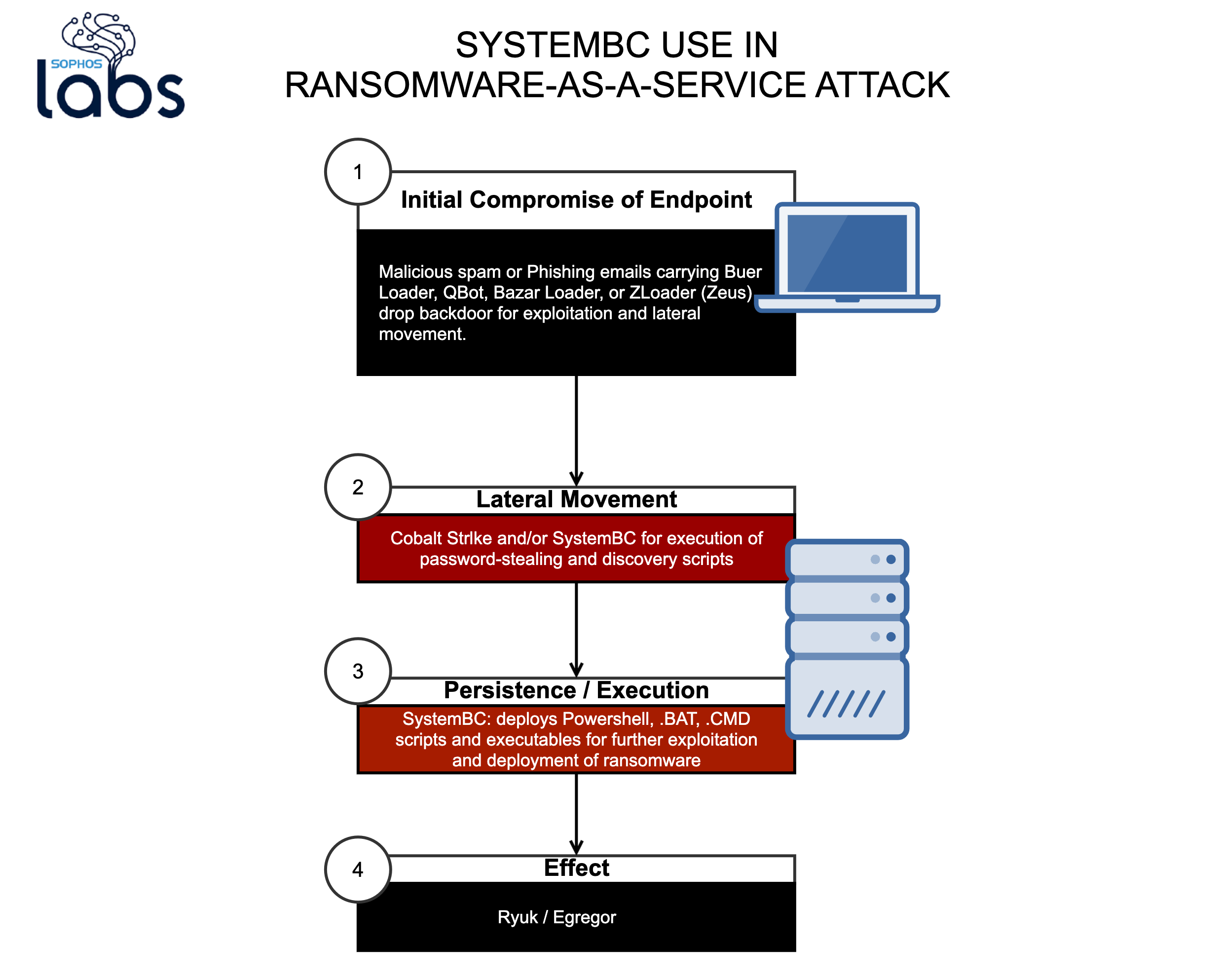
.png?width=5000&name=deadringer-social-02%20(1).png)